МАТЕМАТИЧНЕ ТА КОМП'ЮТЕРНЕ МОДЕЛЮВАННЯ
МАТЕМАТИЧНЕ ТА КОМП'ЮТЕРНЕ МОДЕЛЮВАННЯ
МАТЕМАТИЧЕСКОЕ И КОМПЬЮТЕРНОЕ МОДЕЛИРОВАНИЕ
MATHEMATICAL AND COMPUTER MODELLING
UDK 681.325
Alexander Sokolov, Sergey Chervenko
CODING AND RECONSTRUCTION OF BIT SERIES WITH TAKAGI-SUGENO RECURRENT MODELS
In this paper we investigate the dynamic systems, which are represented by recurrent Takagi-Sugeno rule bases that are widely used in many applications. The main question to be answered is under what conditions the recurrent rule base can reconstruct the chaotic bit series. We use for this purpose so-called "backward interval mapping".
INTRODUCTION
In the simplest case the recurrent Takagi-Sugeno (TS)
fuzzy rule base of 0tfl order can be presented in the following form [1]
R^'.If xk= L^then Ap
R2:Ifxk= L2thenxk+i = A2,
RN:Ifxk = LNthen xk+x= An,
where x G I = [0, 1] is a scalar state variable, Z,(. are linguistic variables (terms), and the Ai E [0,1] are constants. The transition function /(x):/—can be written in the form
f:xk^xk +1- (7)
I may be proved ha hree rules l'ke (1) are necessary and sufficient for producing chaos mapping (if normality conditions are held for membership functions). Then mapping (2) is chaotic in sense of Li-Yorke [2]. When we have
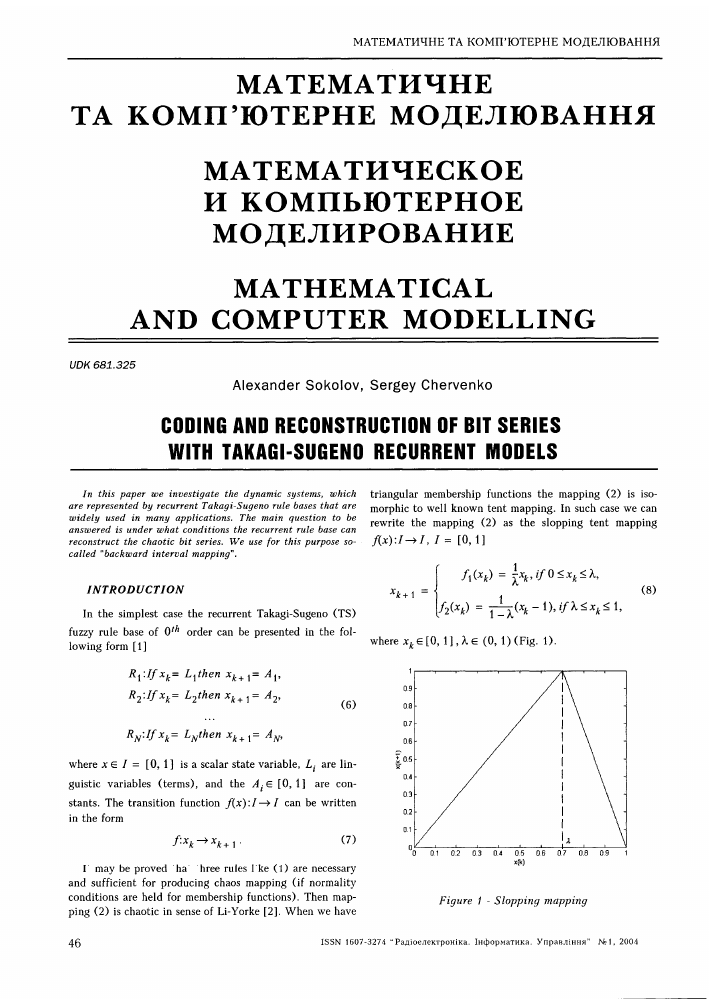
triangular membership functions the mapping (2) is isomorphic to well known tent mapping. In such case we can rewrite the mapping (2) as the slopping tent mapping f(x):I-^I, / = [0,1]
4+ 1
1
(8)
where x. e [0, 1] Д e (0, 1) (Fig. 1).
Figure 1 - Slopping mapping
46
ISSN 1607-3274 "Радюелектрошка. 1нформатика. Управлшня" №1, 2004
CODING OF CHAOTIC BIT SERIES WITH RECUR RENT TAKAGI-SUGENO MODELS
Let us consider the following bit sequence
C={c,.}f=1>
? = ^i-M
according to the rule
c i =
1 ,ifxt>X, 0 ,ifxt>X,
g{x) = f~\x).
The mapping (7) is contracting mapping if f{x) is chaotic.
For (k-\)th step we can write
xk-\ = Sixk).
Because is contracting mapping, then hence
/|U/2 -I and /,u/2 = 0. The second step of backward mapping is
(16)
(9)
with length N,cte {0, 1}.
It is necessary to restore the source sequence (4) as a bit sequence
g2(I) =
(10)
(11)
gl(g(/)) = {^(Z)) = /21 C/2,
g>i8iI)) = g2WD) = /22c/2.
(17)
Lemma
Let there be given g(x) = (g |(x), g2(x)) where g., ¿=1,2 are monotonous and continuous mapping on g{x)\I —» / and g(x) is constructed in the form (10) and it is contracting mapping ((11) is being satisfied) and we have
for i = M,N,M<N.
Namely, it is necessary to find such value xM that gives the same values for restoring sequence like in the source one. Besides, it is important to find such value of A., that gives maximum members of restored sequence. The best case is when M= 1.
The novelty of approach proposed consists in substitution of chaotic bit series by initial value x^ that can reconstruct original orbit with mapping (3).
Underlying methodology is based on so called backward interval mapping.
We propose the following solution of this task. First of all we propose to use socalled backward interval mapping.
Let us consider
g
,K+ 1
(I)
\gX{gK{I)) = IHK} \g2(gK(I)) = I2{K},
(18)
where {.£} = {11...1, 11...2, ...22...2} is set of indexes length of K that were used for marking subset of I on Kth step and the next conditions are fulfilled
,K+ 1/
then
gf^McgftT),* = 0,1,...,
g$+Hi)^gk2(D,K = o,i,...,
g%(I)*0,K = 0,1,...,
(12)
(13)
and g(x) = (g) (x), g2(JC)) contracting mapping for the set I and all of it subsets.
If = (g\(x), g2(x)) is fulfilled to Lemma conditions then f(x) = g~1 (x) is chaotic in sense of definition of Wigging and Devaney.
For slopping tent mapping (3) we have next backward mapping [5] (Fig. 2)
Definition (Wigging and Devaney [3, 4]). Mapping f{x)\I —> I is chaotic if
1. It is topologically transitive, i.e., if there exists a k> 0 such that fk(U)nV*0, where fkU = = {fk{x)\xE U}, for any pair of open sets, U, Veil.
2. It is sensitive to the initial conditions, i.e. if there exists a 8 > 0 such that x£ / and any neighborhood N of x there exists a ye N and n > 0 such that \fn(x)-f"(y)\>8.
3. The periodic points of / are dense in I.
According to this Definition we need to find the topological transitivity for inverse mapping (8) as
g~"(U) n V* 0 . (14)
We use the interval mapping instead of point mapping, namely we consider the mapping
xu =
gi(xk+i) = ^xk+v g2(xk+0 = +
(19)
(15)
Figure 2 - Backward slopping mapping
MATEMATHHHE TA KOMIl'IOTEPHE MOflEJIIOBAHHfl
Let us consider the action of this mapping when argument of function g is interval (Fig. 3). For initial interval I we have
_ \g\{I) = I\ = [0,X]c/
8{f> ~ U200 = h = [M]c/.
1
0.9 0.8 0.7 0.6 >0.5 0.4 0.3 0.2 0.1
Iii
0 0.1 0.2 0.3 0.4 0.5 0.6 0.7 0.B 0.9 1 x(k+1)
Figure 3 - Backward interval slopping mapping
[X, 1 },ifcN= 1, [0,H ifcN= 0.
(21)
"N- 1
'N- 1
ig2(IN)'fCN= 1'
\gx{INWcN= 0.
(23)
diam(IM_ t) = e
(24)
According to (14) total coefficient of con-traction of iterative procedure for backward in-terval mapping is determined as
K = Xn(X-l)m,
(25)
(20)
The following iterative procedure for back-ward interval mapping takes place. Let choose initial interval according to rule
where is quantity of 'zeros' in the source sequence and m is quantity of 'ones' (Fig. 4).
The following statement holds true
arg minX"(X -\)m = n, Àe (0, 1)
Proof
We will find extremum of function K(X) .
K(X) = nX"~l(X- \)m + Xnm(X- \)m~ = X"(^(X-l)m + rn(X-\)m-i
(26)
-0.15
-0.25
-0.35
Then define the possible transitions with the backward interval mapping
rg^cifUL /iV-l = n „ (22)
[gji/jy) c [X, 1].
The next interval is made more precise in according to the value c.
The procedure (17), (18) is repeated until obtaining the limit of accuracy
Then any values x^E IM restore the source sequence (4) with forward mapping (3) form M number of sequence. Parameter E is machine accuracy. In general case it is
8 = (in MatLab, Delphi programming environ-
ment, so on).
So we can not restore arbitrary sequence with backward methods (only for moment when interval became e -length).
To increase the quantity of restoring numbers we need to find optimal value of X .
Figure 4 - Coefficient of contraction in iterative mapping procedure for a special case sequence
We have X i 0, X ï 1 and expression in brackets is equal to the zero in the case X = n .
Indeed
K{n) = rt"((w-l)m + /w(H-l)m-1).
With n + m = 1 we have
K{n) = «"((«- l)m + (1 -«)(« - l)w_ = = «"((«-l)OT-(rt-l)m) = 0.
Statement (21) is proved.
Thus, it is possible to decrease speed of contraction of intervals for iterative backward mapping procedure.
Hence, we have a {0,1} - sequence and a "machine" which is able to reproduce this sequence starting with certain real xO. Thus we have to store only xO (and the "machine", i.e. the tent mapping). If we use slopping tent map we need to extra store X as well and number of elements in series. If we use simple tent mapping it is necessary to store only xO because the maximum elements that can be restored by this method is 48 (in case of simple tent). The initial sequence of {0,1} is restored according algorithm - if chaos (0,1) sequence is greater then X we write 'one' else 'zero'. In simple tent map lambda is 0.5.
48
ISSN 1607-3274 "PaaioejieKTpoHiKa. lHtj>opMaTHKa. YnpaB.iiHHa" №1, 2004
Parame er X s power of slopp ng. I s used for ncreas-ing of number of restoring elements. Labmda is calculated by counting of percent of 'zeros' and 'ones' in the sequence.
EXAMPLE
Let's consider application of the described approach to the coding and restoration of bitmap image (Fig. 5).
Let dark pixels of bitmap be encoded by "ones" and light pixels - by a "zeros". This bit-map was transformed to one-dimensional sequence with the length N=Col*Row by reading all lines from top to bottom.
Figure 5 - Graphic presentation of the letter 'R' Thus we have the next example of bit sequence (4)
c = {111110010001010001011110010100110011}.
Let's define the quantity of "zeros" and "ones" in (15) for optimum slopping tent mapping construction
n = 17/36 = 0.472222222222222, m = 19/36 = 0.527777777777778.
Thus in equation (3)
X = 0.472222222222222. According to rule (16) initial interval /g6 is defined as
/36 = [X, 1] = [0.472222222222222,1].
In accordance with iterative rules (17) and (18) the next interval is
735 = S2(!3e) =
=[0.472222222222222,0.750771604938272]. The next step of iterative procedure gives
735 = S2(h6) = Sl(735) = = [0.222993827160494,0.354531035665295].
Figure 6 - Graph of chaotic mapping
Table 1
Step x(k) C c
1 0.67260452606 1 1
2 0.620328266412631 1 1
3 0.719378021533962 1 1
4 0.531704801304073 1 1
5 0.887296165950178 1 1
6 0.213544106620716 0 0
7 0.452211049314457 0 0
8 0.957623398548262 1 1
9 0.0802925080138202 0 0
10 0.170031193441031 0 0
11 0.360066056698654 0 0
12 0.762492825950091 1 1
13 0.450013592936669 0 0
14 0.952969961512947 1 1
15 0.0891095466070482 0 0
16 0.188702569285514 0 0
17 0.399605440839912 0 0
18 0.84622328648452 1 1
19 0.291366404555647 0 0
20 0.617011209647253 1 1
21 0.725662971194679 1 1
22 0.519796475631135 1 1
23 0.909859309330481 1 1
24 0.170792887584352 0 0
25 0.361679056060981 0 0
26 0.765908589305606 1 1
27 0.443541620263062 0 0
28 0.939264607615896 1 1
29 0.115077585569881 0 0
30 0.243693710618572 0 0
31 0.516057269545212 1 1
32 0.916944120861703 1 1
33 0.157369034156774 0 0
34 0.333252072331992 0 0
35 0.705710270820688 1 1
36 0.557601592129222 1 1
МАТЕМАТИЧНЕ ТА КОМП'ЮТЕРНЕ МОДЕЛЮВАННЯ
The final result of implementation of our iterative procedure is
Ix = [0.672604526057511,0.672604526072895].
As you can see
diam{Ix)= 1.53835832961136«-01 l>e =le-15, that's why in our example M = 1.
Now if we choose any x^E I^ we can restore a bit sequence using chaotic mapping (3) and rule (6). For example if x^ = 0.67260452606 then slopping tent mapping (3) give us chaotic sequence shown on Fig. 6.
We know value of X and according to rule (6) can restore all members of target sequence as it is shown in Table 1.
CONCLUSION
Approach proposed can be used for coding and data compression as well. We can increase the amount of encoded elements for bit sequence with few "ones" or "zeros" in it, because reduction of total coefficient of contraction takes place in such case. Obviously that critical factor of the algorithm is accuracy of software and hardware. It depends on sensitivity to initial conditions of chaotic mapping.
REFERENCES
1. R. Kempf, J. Adamy, "Regularity and chaos in recurrent fuzzy systems", Fuzzy Sets and Systems, vol. 140, 2003, pp. 259-284.
2. T.Y. Li, J.A. Yorke, "Period three implies chaos", Amer. Math. Monthly, vol. 82, 1975, pp. 985-992.
3. P.E. Kloeden, "Cycles and chaos in higher dimensional difference equations", Proceedings of the 9th Internet. Conf. Nonlinear Oscillations, Vol.2, Kiev, Naukova Dumka, 1984, pp. 184-187.
4. P.E. Kloeden, "Chaotic iterations of fuzzy sets", Fuzzy Sets and Systems, vol. 42, 1991, pp. 37-42.
5. A. Sokolov, M. Wagenknecht, "Investigation of chaotic behavior of fuzzy Takagi-Sugeno models with regard to simulation and control of technological processes", Scientific Report, Univ. of Zittau/Goerlitz, IPM, 2003.
НадШшла 26.03.04
В данш po6omi ми дос.'пджуемо динамгтп системи, що представленг рекурентними базами правил ТакагиСугено, ят широко використовуютъся для багатьох застосувань. Головне запитання, на яке необх1дно eidnoeicmu, - в яких умовах рекурентна база правил може реконструювати хаотичш 6imoei nocjiidoeuocmi. Ми використовуемо для досягнення щег мети так зване "зворотне хаотичне в1дображення".
В данной работе мы исследуем динамические системы, которые представлены рекуррентными базами правил Та-каги-Сугено, широко использующимися во многих применениях. Основной вопрос, на который необходимо ответить, -в каких условиях рекуррентная база правил может реконструировать хаотические последовательности бит. Мы используем для достижения этой цели так называемое "обратное интервальное отображение".
УДК 519.71
В.В. Бескоровайный
СИНТЕЗ ТОПОЛОГИИ ТЕРРИТОРИАЛЬНО РАСПРЕДЕЛЕННЫХ СИСТЕМ С КОЛЬЦЕВЫМИ СТРУКТУРАМИ
Рассматривается задача синтеза топологии территориально распределенных систем в классе кольцевых (радиально-кольцевых) структур с расширенным набором оптимизируемых параметров и ограничений. Предложены математическая модель и метод решения задачи. Приведены оценки временной сложности и точности предложенного метода.
ВВЕДЕНИЕ
Задача оптимизации топологии является одной из основных при синтезе территориально распределенных объектов [1]. Существует множество систем, принципы построения и особенности технологий функционирования которых предполагают их построение по кольцевым схемам. Учет ограничений на производительность центра, пропускные способности связей, длины кольца и т.д. в задачах синтеза кольцевых структур на практике приводит к формированию сетей кольцевых подструктур с единым центром. При этом в предельном случае образу-
ется радиально-кольцевая структура с количеством кольцевых подструктур равным количеству элементов системы. Типичным примером могут служить топологические структуры специализированных компьютерных сетей, транспортных систем для развозки почты, товаров, доставки билетов [2].
Постановки задач структурного синтеза подобных систем имеют много общего с постановками задачи коммивояжера (ЗК) [3]. Вместе с тем, они включают специфические факторы, не позволяющие напрямую использовать методы решения задач синтеза кольцевых структур: учет трафика между элементами; выбор места расположения центрального узла; определение количества подструктур; разбиение множества элементов на подструктуры; учет ограничений по каждой из подструктур.
Для решения задач, сводимых к ЗК, известно множество точных и приближенных методов [4, 5]. Они зачастую неприменимы для решения задач структурного синтеза с учетом перечисленных факторов.
50 ISSN 1607-3274 "Радюелектрошка. 1нформатика. Управлшня" №1, 2004





 CC BY
CC BY 8
8